1. CypSec’s Cyber Deception Service
In the evolving threat landscape, traditional defensive methods often fall short of detecting sophisticated attackers. CypSec’s cyber deception service introduces a proactive layer of defense by creating a dynamic and deceptive environment that misleads and traps attackers. This service is designed to detect and analyze adversary behavior in real time, offering organizations valuable insights into ongoing threats while protecting critical assets. By simulating enticing targets, the cyber deception service helps expose attackers early, limiting their ability to cause damage.
Key Benefits
- Proactive Detection: Detect attackers early in their efforts by diverting them into deceptive environments, reducing their ability to cause harm to critical assets.
- Behavioral Insight: Gain valuable insights into adversary techniques and tools through continuous monitoring of deceptive environments.
- Automated Deployment: Quickly deploy decoys and honeypots across cloud, on-premise, or hybrid environments, ensuring comprehensive coverage.
- Integrated with Threat Intelligence: Correlate adversary behavior with real-time global threat data, enhancing the organization’s threat intelligence capabilities.
- Regulatory Compliance: Meet industry regulations with detailed logs, early detection of unauthorized access, and real-time monitoring of suspicious activities.
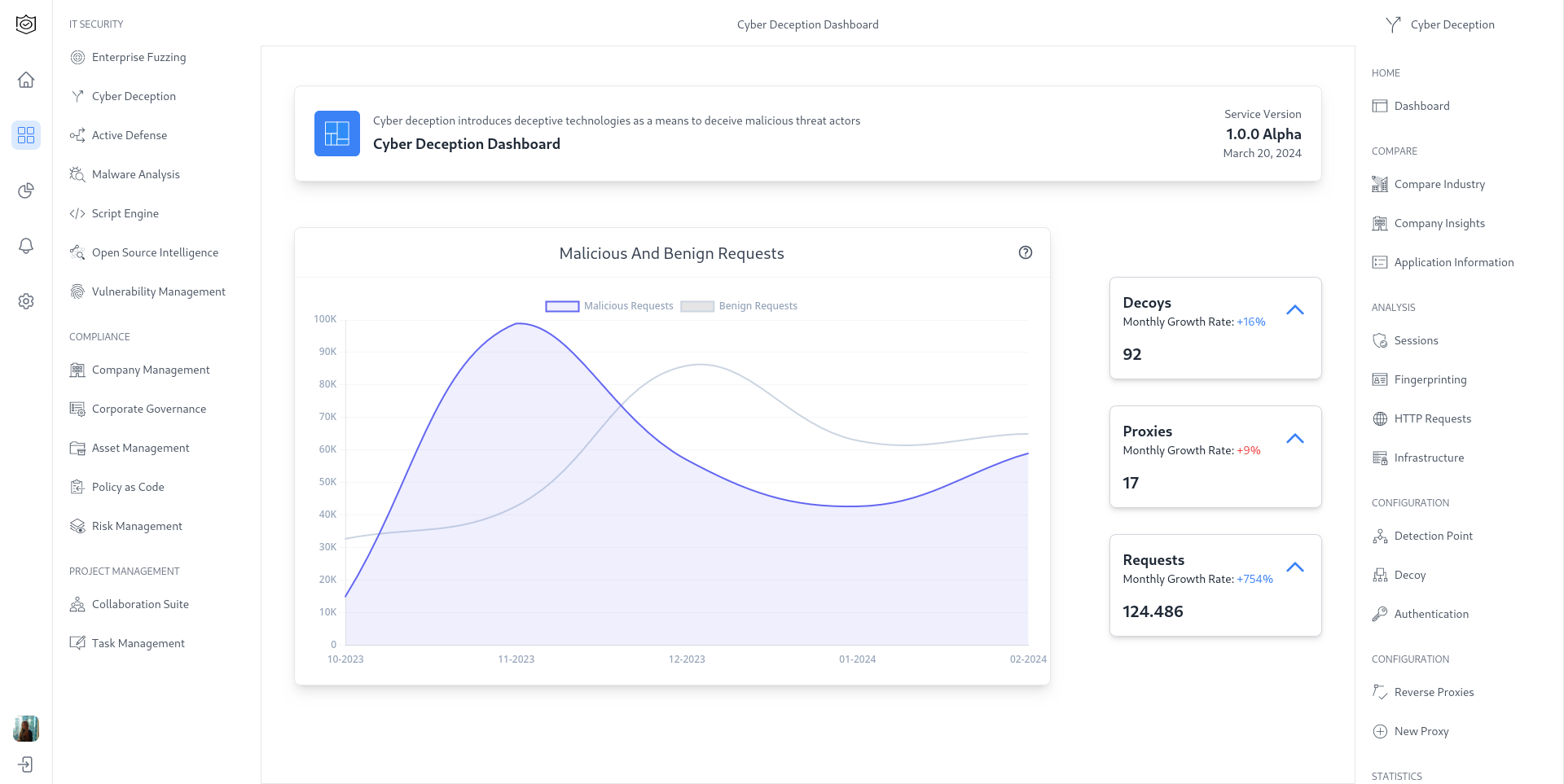
2. Core Features
Deceptive Environments
At the heart of CypSec’s cyber deception service is the deployment of deceptive environments that mimic real systems, applications, and networks. These decoys, or "honeypots," are designed to appear as valuable targets to attackers. They seamlessly blend into the organization’s infrastructure, making it difficult for intruders to distinguish between genuine assets and deceptive traps. This allows security teams to observe attacker behavior and gather intelligence without risking real systems.
Deceptive Technologies for Active Defense
The service integrates deceptive technologies with CypSec’s active defense service, providing a more resilient and proactive security posture. By deploying decoy systems and vulnerable-looking services, the platform diverts attackers away from real assets. These decoys are equipped with sensors and monitoring tools to capture attack vectors, methods, and patterns used by adversaries, offering organizations real-time insights into the tactics employed by attackers.
3. Behavior Analysis and Threat Intelligence
Adversary Behavior Analysis
One of the key advantages of cyber deception is the ability to monitor attacker behavior without alerting them. CypSec’s cyber deception service records every action an attacker takes within the deceptive environment. This information is used to perform behavioral analysis, identifying key indicators of compromise (IOCs) and mapping out attacker techniques. This intelligence is invaluable for strengthening defenses and updating response strategies.
Threat Intelligence Integration
The cyber deception service integrates with CypSec’s broader threat intelligence platform, allowing data collected from deceptive environments to be cross-referenced with known threats. This integration helps organizations stay ahead of emerging threats by automatically correlating suspicious activity with global threat data. By combining deception with real-time threat intelligence, organizations can take a proactive stance in mitigating risks before they escalate.
4. Automation and Detection
Automated Deception Deployment
CypSec’s cyber deception service offers automated deployment of deceptive environments, ensuring quick and scalable implementation across complex infrastructures. Organizations can deploy honeypots, decoys, or vulnerable services across cloud environments, on-premise networks, or hybrid infrastructures. The service’s scalability makes it suitable for both small businesses and large enterprises, offering comprehensive coverage of attack surfaces.
Early Attack Detection and Response
Cyber deception is particularly effective in early attack detection. By luring attackers into interacting with deceptive environments, the platform can detect intrusions at an earlier stage than traditional defenses. Once an attacker interacts with a decoy, automated alerts notify security teams, allowing for an immediate response. This early detection reduces the attacker’s ability to compromise real assets and provides security teams with valuable lead time to contain the threat.
5. Security and Compliance
Minimizing Attack Impact
By diverting attackers away from critical systems, CypSec’s cyber deception service significantly reduces the impact of cyberattacks. Even if attackers breach the perimeter, they are funneled into deceptive environments, limiting their ability to cause harm. This proactive approach helps organizations mitigate the risks associated with data breaches, ransomware attacks, and insider threats. The service’s integration with CypSec’s Security Operations Center (SOC) ensures continuous monitoring and analysis of attack patterns, further minimizing potential damages.
Support for Regulatory Compliance
Many industry regulations, including NIS2, GDPR, and ISO 27001, require businesses to implement advanced security measures to protect sensitive data. CypSec’s cyber deception service helps organizations meet these requirements by providing real-time detection of unauthorized access and early warning systems for potential breaches. The service’s ability to capture detailed logs and generate forensic data also ensures that organizations have the necessary information for regulatory audits and post-incident reviews.
6. Interconnected Ecosystem
Integration with Risk Management
CypSec’s cyber deception service works in tandem with the risk management and vulnerability management services, providing a comprehensive security framework. Vulnerabilities identified through fuzzing or vulnerability management can be replicated in deceptive environments, allowing organizations to study how attackers might exploit them. This integration ensures that deception strategies are aligned with the organization’s overall risk profile, enhancing the ability to address real-world threats.
Enhancing Incident Response
The data collected by CypSec’s cyber deception service is invaluable for incident response teams. The service integrates seamlessly with CypSec’s incident response tools, providing security teams with detailed information on attacker behavior, tools used, and compromised systems. This information allows for faster and more effective mitigation strategies. By integrating with the Script Engine, the service can automate responses, such as isolating compromised systems or triggering forensic analysis.
7. Customization and Scalability
Customizable Deception Campaigns
CypSec’s platform offers fully customizable deception campaigns, allowing organizations to design tailored deceptive environments that match their infrastructure. Administrators can define the types of decoys to deploy, whether they be vulnerable applications, open ports, or misconfigured services. This customization ensures that deception efforts are relevant to the specific threat landscape the organization faces and provides more targeted threat intelligence.
Scalable for Complex Networks
Whether deployed across a small network or a global enterprise, CypSec’s cyber deception service is designed to scale. The platform supports the deployment of hundreds of deceptive systems, each integrated into the broader security infrastructure. As businesses grow, so do their deception capabilities, ensuring that all segments of the organization’s digital landscape are covered.
8. Conclusion
CypSec’s cyber deception service provides a proactive defense strategy that goes beyond traditional security measures. By creating dynamic and deceptive environments, organizations can lure attackers away from critical assets, observe their behavior, and gather valuable intelligence. The integration with CypSec’s broader security services, including risk management, vulnerability management, and incident response, ensures that businesses maintain a resilient and secure infrastructure. Whether addressing insider threats, sophisticated attackers, or unknown vulnerabilities, the cyber deception service enhances an organization’s ability to detect, analyze, and respond to threats in real-time.